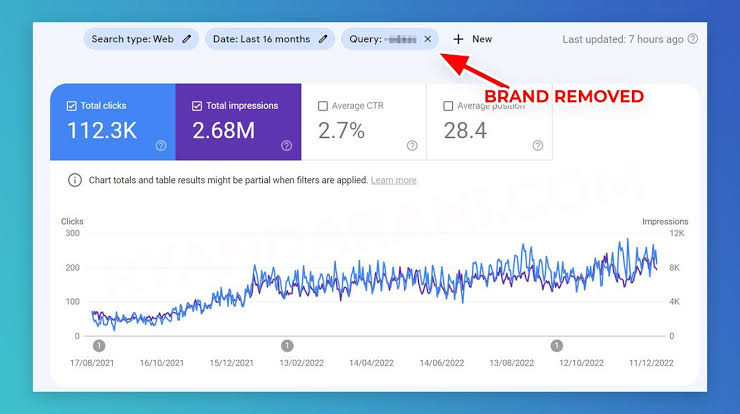
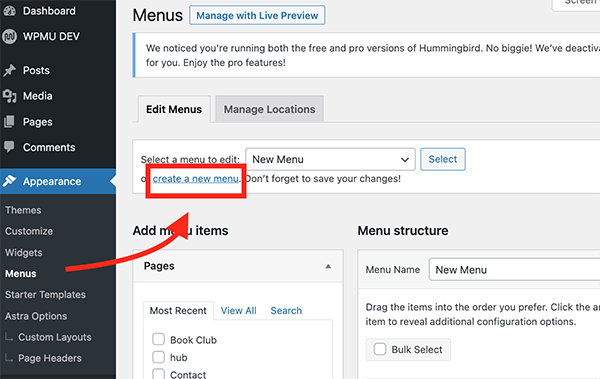
Top Ethical Hacking Tools in the year 2023
Invicti Is a web application security scanner hacking tool to find SQL Injection, XSS, and vulnerabilities in web applications or services automatically. It is usually available on SAAS solution Features:It detects Dead accurate vulnerability with the help of unique Proof-Based Scanning Technology.It requires minimal configuration with a scalable solution. It automatically detects URL rewrite rules…