Amazon slapped With $2.5B Penalty for Deceptive Prime Sign-Ups
The Federal Trade Commission (FTC) has reached a $2.5 billion settlement with Amazon over what it calls “deceptive” Prime subscription practices. Of that amount, $1.5 billion will be set aside for refunds to millions of customers who were either signed up for Prime without their consent or found it nearly impossible to cancel, according to…

How diagnosis image annotation turns scans into insights in the world of data science
A skilled radiologist leverages medical imaging technology to evaluate cancer risk factors, guiding an elderly female patient toward early detection and preventative treatment options. The Critical Role of Diagnostic Image Annotation in Medical AI A radiologist may spend hours scanning through hundreds of CT images, searching for a tiny shadow that could indicate cancer. In…
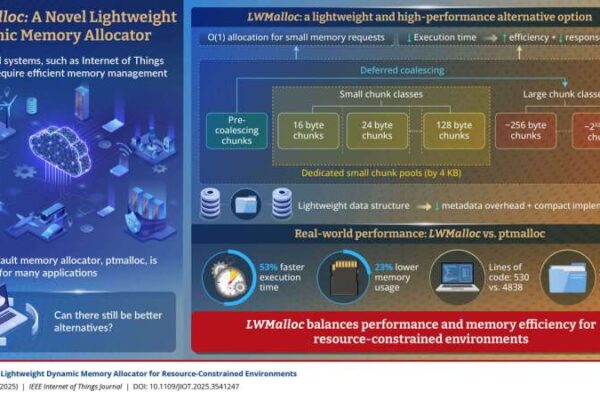
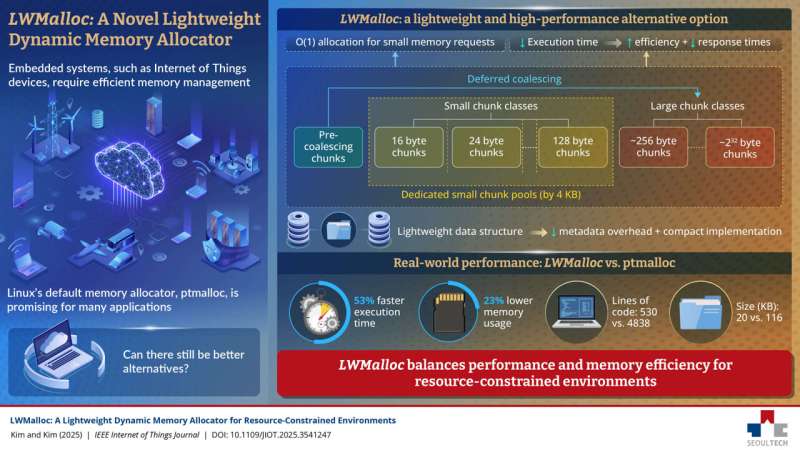
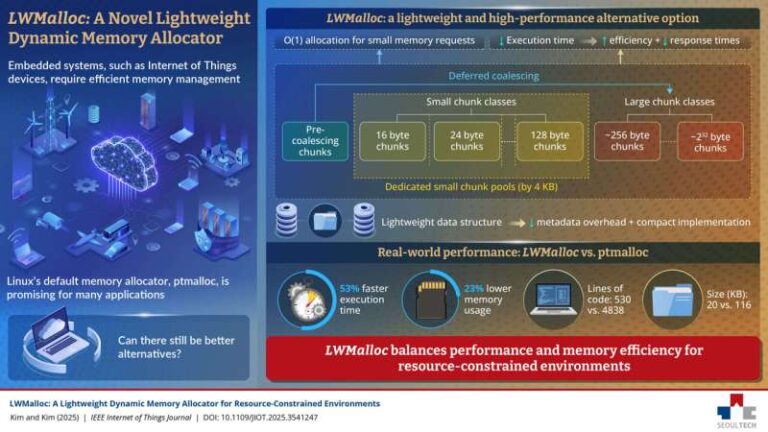
How Ultra-lightweight memory allocator is enhancing performance of IoT and embedded systems in the world
Embedded systems—such as Internet of Things (IoT) devices and single-board computers—often operate under strict memory and processing limitations, making efficient resource management essential. Linux, with its flexibility and cost-effectiveness, has become a popular choice for these platforms. Variants like Ubuntu Core, Raspberry Pi OS, BalenaOS, and OpenWrt are widely deployed across embedded devices. However, Linux’s…
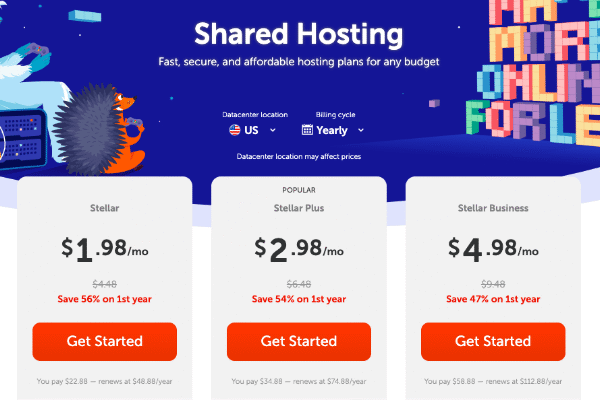
12 Benefits You Gain in a Namecheap Hosting Plan
1. Affordable Pricing – Namecheap stands out as one of the most cost-effective hosting providers in the industry. Many companies offer low introductory prices but hide expensive renewal fees, leaving customers frustrated. Namecheap, however, is transparent about its pricing and ensures that even small businesses, startups, and individuals can comfortably afford to host their websites….

LastPass Warns of Fake Repositories Infecting macOS with Atomic Infostealer
LastPass has issued a warning about a widespread information-stealing campaign targeting macOS users through fake GitHub repositories. These repositories host malware-infused programs disguised as legitimate tools. According to Alex Cox, Mike Kosak, and Stephanie Schneider from the LastPass Threat Intelligence, Mitigation, and Escalation (TIME) team, the fraudulent repositories specifically redirect victims to download the Atomic…

Apple in the Big Shift: iPhone 17 Production Moves to India
For almost ten years, Apple has been looking for ways to reduce its heavy reliance on China for iPhone production. Now, with the launch of the iPhone 17, the company is making its boldest move yet. According to Bloomberg, all four iPhone 17 models — including the premium Pro versions — will be manufactured in…

Here are Advantages and challenges of AI in the Business
Volume 1: Introduction – The Rise of AI in Business In today’s digital era, artificial intelligence (AI) has quickly shifted from being an experimental technology to becoming an everyday necessity in the business world. What was once limited to academic research and advanced laboratories has now made its way into almost every industry, reshaping how…

Mastercard Advances AI-Powered Payments with New Tools & Collaborations
Mastercard is partnering with AI and commerce leaders, including Stripe, Google, and Ant International’s Antom, to enable secure, scalable agentic transactions for digital merchants and platforms worldwide. The company is advancing AI-driven payments by offering new developer tools, expanding consulting services, and fostering collaborations within the global tech and finance communities. All U.S. Mastercard cardholders…
ChatGPT Revolution: New Software Integrations Reshaping Digital Assistance
WhatsApp Integration: OpenAI has introduced ChatGPT to WhatsApp, allowing users to interact with the AI directly within the messaging app. By adding the number +1 (800) 242-8478 to your contacts, you can chat with ChatGPT without needing a separate application. This integration aims to make AI assistance more accessible, especially in regions with limited internet…

Tech Giants Unveil Innovative Solution to Shape the Future of Connectivity
In response to the growing need for customizable and affordable connectivity, Cisco and NTT DATA have teamed up to enhance wireless connectivity for global enterprises, offering a unified solution supported by the robust services of both companies. Traditionally, landlines have been the primary method for connecting business spaces. However, with the advent of eSIM technology,…

How Fintech is Changing: Insights from Clinton Leask of Pay@
In today’s fast-paced world, brands understand that every touchpoint in the consumer journey is crucial—especially in the payment process. This has never been more evident as consumers expect more convenience and personalization at every step. As 21st-century shoppers, we are truly spoiled for choice. Offering a range of optimized, personalized, and integrated payment solutions to…

Here is an Amazing Automated patch management way to stay proactive to cyber attacks
The Growing Need for Automated Patch Management Cyberattacks are becoming increasingly frequent and sophisticated. According to a report from the International Monetary Fund, global cybercrime costs are expected to reach $23 trillion by 2027—an alarming 175% increase from 2022. This surge makes effective patch management more critical than ever. However, traditional manual methods are too…

Paid Training, Placement Program Eases Cybersecurity Hiring Challenges
Despite businesses and individuals implementing secure computing practices, hacker breaches targeting both corporate and personal data continue to escalate, underscoring significant gaps in cybersecurity expertise. To address this, NukuDo, a cybersecurity workforce developer, is tackling these gaps by offering specialized training programs that guarantee employment in the field of computer security. The U.S. is grappling…
IBM’s New Environmental Intelligence Platform Delivers Data Via APIs
IBM has launched a beta version of its Environmental Intelligence (EI) platform, offering application developers and data scientists AI-powered environmental insights, along with access to open-source geospatial and satellite data. This cloud-based platform provides a wide range of geospatial, weather, and climate APIs, enabling users to build applications that tackle sustainability challenges, climate change, and…
If AI is the Future of Business, Why Are So Many Struggling to Harness Its Power?
Generative AI: The Spotlight of Innovation Generative AI has emerged as one of the most transformative technological advancements in recent years. However, two pressing questions arise: why is it gaining such widespread attention now when companies like AWS and Synthesis Software Technologies have been using it for years? And why do so many businesses struggle…

Fraud| why Shared Intelligence is the Key to Staying Ahead
According to the latest Global State of Fraud Report from LexisNexis® Risk Solutions, banks and online retailers can significantly improve their ability to detect hard-to-identify, high-risk fraud by integrating shared fraud intelligence into their risk assessment processes. The report emphasizes how collaborative digital identity intelligence can help businesses build stronger digital trust and proactively prevent…

Switzerland debuts ePost encrypted platform in a digital world
Switzerland’s national postal service, Swiss Post, aims to attract one million residents to its ePost encrypted communication platform by the end of 2025. Facing a steady decline in demand for traditional mail, Swiss Post is positioning ePost as a comprehensive mobile app to bridge the gap left by reduced postal usage. ePost aspires to become…

US watchdog issues final rule to supervise Big Tech payments
by shadjava Tech companies like Apple, Google, and PayPal, along with other digital payment services that handle over 13 billion financial transactions annually, will now face government oversight, according to a new rule from the U.S. Consumer Financial Protection Bureau (CFPB). Announced on Thursday, the rule subjects digital wallets and payment apps to the same…

Adobe announces development of SLM that can run locally on a phone with no cloud connection
A small team of AI researchers from Adobe Inc., in collaboration with colleagues from Auburn University and Georgia Tech, has developed a compact language model (SLM) they claim can operate entirely on a smartphone without relying on cloud services. The team has released a paper detailing their innovation, named SlimLM, on the arXiv preprint server….

Thrilling SpaceX’s Launch from KSC in a Canaveral Mission Ready to Soar Today
SpaceX launched a Falcon 9 rocket on Sunday evening from Kennedy Space Center’s Launch Pad 39-A as part of the Optus X/TD7 mission. The mission, aimed at deploying a geostationary communication satellite for Australian company Optus, was built by Northrop Grumman. Liftoff occurred at 5:28 p.m. ET, marking the 16th flight for the Falcon 9’s…
Here is How robotics can be used to better understand the ‘sense of self’ in humans
In a recent review published in Science Robotics, a cognitive roboticist, cognitive psychologist, and psychiatrist explore the fascinating concept of “sense of self” in humans and how robots could offer new insights into this phenomenon. The experience of being a self—connected to our bodies and capable of interacting with the world—feels natural to us as…
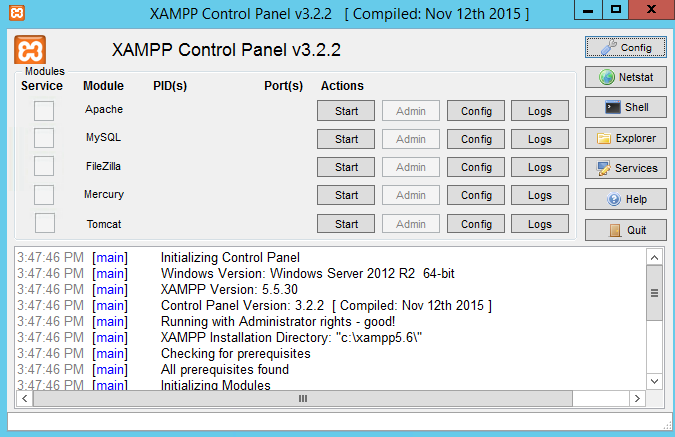
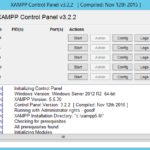
Here is How to Run a PHP File Using XAMPP
Introduction to PHP and XAMPP PHP is a widely-used, open-source server-side scripting language for web development. However, running a PHP project requires a web server, even for locally developed webpages. Among the available options for setting up a local web server, XAMPP and WampServer are the most popular choices. While WampServer is exclusive to the…

Here is How to Install a Node.js Application
Installing a Node.js Application Pre-Installation Settings Before you begin, ensure your hosting provider has installed the necessary EasyApache 4 packages for your server. Required and Recommended Packages Operating System Required Packages Recommended Packages AlmaLinux 8 / Rocky Linux 8 Required:1. ea-ruby27-mod_passenger (disables Apache’s mod_userdir module).2. ea-apache24-mod_envChoose one:– ea-nodejs16– ea-nodejs18– ea-nodejs20– ea-nodejs22 ea-ruby27-ruby-devel AlmaLinux 9 /…
Here are amazing steps for Hosting a Website on GitHub:
Setting Up a Custom Domain (Optional)

Top 10 Computer Softwares in the field of IT
10 Computer Software Examples (Plus Definitions and FAQs)Updated October 12, 2024 Computer software plays a crucial role in ensuring your devices function properly and help you achieve your goals. Whether for professional or personal use, understanding the various types of software can help you choose the right tools for your needs. In this article, we’ll…
Amazing serverless computing in the|DevOPs
The Rise of Serverless Computing: Embracing Speed Without Sacrificing Control Achieving the right balance is key. With the right tools and processes in place, developers can maintain strong governance standards while also unlocking greater agility, cost efficiency, and creative potential within serverless environments. This enables them to move quickly and innovate, without sacrificing control or…
New machine learning model unveiled|fake news detector
Fake news remains a persistent challenge, particularly during election seasons when conspiracy theories and misinformation from malicious sources seek to sway voters. As the US election heats up in one of the tightest races yet, researchers at Ben-Gurion University of the Negev have created a method to assist fact-checkers in managing the surge of misinformation…
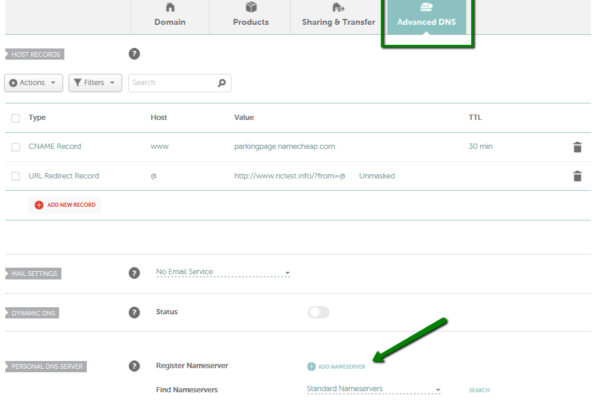
Here’s a practical guide on changing nameservers for your domain.
Step-by-Step Guide to Changing Nameservers Let’s say you bought your domain from GoDaddy and are hosting with HostGator, which gave you the following nameservers: ns1.hostgator.com ns2.hostgator.com Here’s how to change your nameservers in GoDaddy: Go to GoDaddy’s website. Enter your login credentials to access your account. From your dashboard, find and click on “My Products.”…

JetBrains debuts Amazing AI model in the software industry
JetBrains has introduced Mellum, its proprietary AI model tailored for software development tasks. Mellum is exclusively integrated into JetBrains’ AI Assistant, delivering significant enhancements in both the speed and accuracy of code completions compared to earlier versions. In contrast to larger language models, Mellum is designed with a smaller footprint to provide near-instant coding suggestions….

Putin’s symbolic banknotes in the world of…
At the BRICS summit in Kazan, Russia, a symbolic banknote was unveiled, sparking discussions about reshaping global finance. Featuring the flags of Brazil, Russia, India, China, and South Africa, the note represents these nations’ ambitions to explore alternatives to the US dollar for cross-border transactions. Russian President Vladimir Putin emphasized that while the BRICS nations…

BTC track in the longest flat market halving year history
Bitcoin (BTC) is on track to possibly have its longest period of sideways trading during a halving year if it doesn’t show significant upward movement in the next two weeks. According to a dashboard shared by CryptoQuant CEO Ki Young Ju, the longest time BTC previously took to rise was 298 days. In 2020, Bitcoin…

OpenAI Partners Global Media Giant in a…
seeking advanced AI Solutions OpenAI has teamed up with Hearst, one of the largest and most varied media companies in the world. This partnership aims to enhance both companies’ products by integrating Hearst’s extensive collection of newspapers and magazines into OpenAI’s offerings, like ChatGPT. Announced on Tuesday, the collaboration will see OpenAI use content from…
World’s first Fault localization in the software development unveiled
In many software companies, developers often spend a significant amount of their time manually searching for faults, with studies showing this process can consume between 30% to 90% of total development time. Birgit Hofer and Thomas Hirsch from the Institute of Software Technology at Graz University of Technology (TU Graz) have created a solution leveraging…
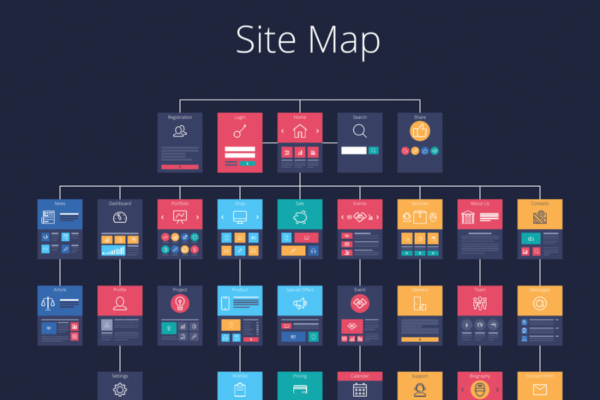
why site maps are important in the websites
Googlebot moves from one page to another, gathering information about the links it encounters and how they’re connected. Google uses this data to generate search results and to figure out what content is most relevant for specific searches. Given how popular Google is and how important organic traffic is, it’s crucial to help this bot…

Here are amazing tips on basic Hacking Techniques
Phishing is a tactic used by cybercriminals to steal sensitive information, such as passwords or credit card details, by posing as a trustworthy source. They trick individuals into clicking on links that lead to fake websites designed to capture their data. These attacks often create a sense of urgency—claiming there’s a security issue or a…

Here are countries expected to use AI in amazing ways to try to influence the U.S. election| Russia, Iran & China
The U.S. is increasingly concerned about threats from Russia, Iran, and China trying to influence the upcoming Nov. 5 elections, particularly through the use of artificial intelligence to spread false or divisive information, as outlined in an annual threat assessment released on Wednesday. The Department of Homeland Security (DHS) report highlights that Russian “influence actors”…

M-KOPA hits $1.5bn in a 5 country credit base
M-KOPA, a fintech company, has reached a major milestone, surpassing 5 million customers across Ghana, Kenya, Nigeria, South Africa, and Uganda. Impressively, 2 million of these customers have joined in just the last 15 months. The company shared that it has provided over $1.5 billion (Sh192 billion) in financing to its customers, as highlighted in…

Here are some of the best IT courses on Udemy, organized by popular categories:
1. Programming & Software Development 2. Web Development 3. Cloud Computing & DevOps 4. Cybersecurity 5. Data Science & Machine Learning 6. Networking 7. IT Support & Help Desk These courses are well-regarded for their quality, hands-on projects, and value for both beginners and professionals looking to upskill or get certifications in the IT field….

Amazing competition in the banking sector
Like any technology, cardless ATMs have their pros and cons. Advantages of Cardless ATMs Disadvantages of Cardless ATMs Banks Offering Cardless ATM Access Several banks provide access to cardless ATMs, including: How to Use a Cardless ATM Using a cardless ATM varies by institution and technology, but generally involves the following steps: Security Considerations for…

India’s court in a standstill | crypto hackers
The official YouTube channel of the Supreme Court of India, which was used for streaming proceedings, was reportedly hacked on Friday and displayed cryptocurrency advertisements. Videos related to a cryptocurrency product were uploaded to the channel, but the entire page has since been removed. The Supreme Court had been using the platform to live broadcast…

Best 6 React IDEs & Editors in the year 2024
1 Visual Studio Code As a software developer, I’ve used many tools, but Visual Studio Code stands out as one of the most impressive. This powerful and versatile code editor is ideal for React development due to its lightweight design and speed. Its built-in debugging features are robust, making it easy to debug React applications,…
Enfusion vs investment bankers in a deep talk
Enfusion (ENFN.N), a U.S. software provider for asset managers, is exploring options, including a possible sale, as it engages with investment bankers, according to sources familiar with the situation. The Chicago-based company, valued at $1.1 billion, began interviewing investment banks recently after attracting interest from potential buyers, including private equity firms, with sources requesting anonymity…

Top SEO analysis tools in the year 2024
Google Search Console is a free tool from Google that allows webmasters to keep an eye on their site’s presence in search results. It provides essential insights about your search traffic, indexing status, and any issues that might affect your site. You can submit sitemaps, check for crawl errors, and view the search queries that…
anti-bullying prevention tool in the year 2024
As of September 16, 2024, TikTok has rolled out some important updates aimed at preventing bullying on the platform. One of the key changes is a simpler reporting process, which makes it easier for users to flag bullying behavior. Now, when someone encounters harmful content, they can categorize their reports more specifically, helping TikTok respond…

Best gaming and coding laptops in the year 2024
1. Dell XPS 15 Our top choice Specifications Display: 15.6″ touch display 3.5K (3456X2160) OLED CPU: 13th Gen Intel® Core™ i9-13900H Graphics: NVIDIA® GeForce RTX™ 4070 RAM: 32 GB DDR5 Storage: 1TB SSD Weight: 4.23 pounds Battery life: 8 hours and 3 minutes Today’s Best Deals Check Amazon Reasons to buy + Sleek display+ Powerful processor and performance+ Outstanding battery life+ Moderately…

Free and premium softwares in grahic design
Free Graphic Design Software Premium Graphic Design Software

What Is a Bespoke Website in Web Design?
A bespoke website design refers to a custom-built website created specifically for a particular client or business. Unlike template-based designs, which use pre-made layouts and elements that can be adapted to various users, a bespoke design is tailored to meet the unique needs, preferences, and goals of the client. Here’s what typically sets a bespoke…
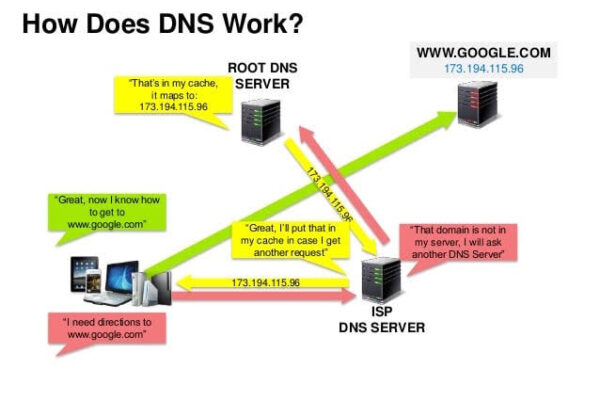
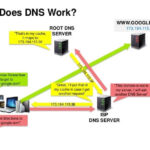
The Power of Nameservers and DNS for a Seamless Website Migration
Nameservers vs. DNS: Thinking of migrating your site to a new hosting provider? Concerned about how it might affect your domain registration? The good news is that with a basic understanding of nameservers and DNS, you can ensure that your transition is smooth without affecting your website’s accessibility. This guide will walk you through the…

Huawei launches $2,800 trifold in the new battle with Iphone
BEIJING — Huawei, the Chinese smartphone giant, announced on Tuesday that its new trifold smartphone, the Mate XT, will be priced starting at over $2,800. Pre-orders for the Mate XT began on Saturday, with in-store sales scheduled to commence on September 20th, the same day Apple’s new iPhone 16 series will hit stores worldwide, including…

Apple debuts iPhone 16 Pro and iPhone 16 Pro Max in the smartphone world
Apple has introduced the iPhone 16 and iPhone 16 Plus, designed with the all-new A18 chip and built for Apple Intelligence, a personal intelligence system that offers relevant, helpful insights while ensuring user privacy. The new models feature Camera Control for enhanced photography, an Action button for quick access to key functions, and a significant…
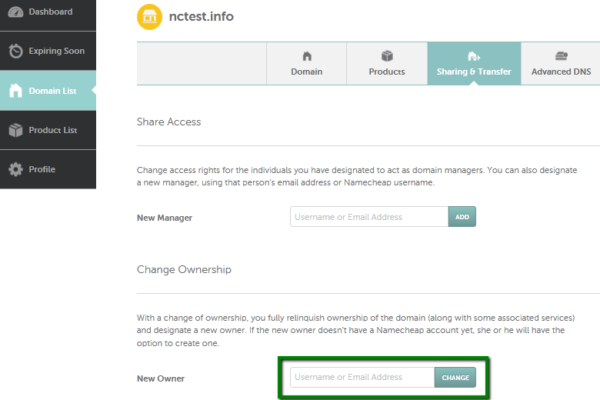
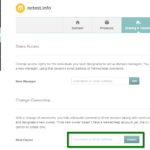
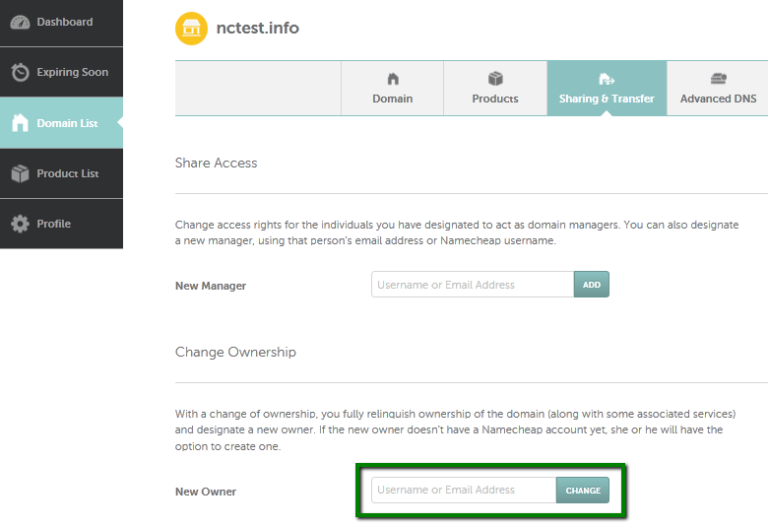
How to move a domain from one Namecheap account to another
You can move a domain to another Namecheap account using the Change Ownership option. Once the domain is completely moved to another account, the new domain holder becomes responsible for all the domain payments. Some tips that should be considered before a domain push: 1) You don’t have to wait for 60 days to move a domain to another Namecheap…

24 New Technology Trends in 2024: Exploring the Future
As technology advances at an unprecedented pace, it is not only reshaping industries but also fundamentally altering the role of IT professionals. In this fast-evolving landscape, staying relevant requires continuous learning, unlearning, and relearning. By 2024, IT professionals must embrace this dynamic environment, constantly updating their skills to thrive in a contactless, digital-first world. So,…

Space-X’s Starlink internet is the Game changer in Kenya
Elon Musk’s satellite internet service, Starlink, has launched a new, more affordable data plan in Kenya, intensifying competition with Safaricom and Airtel, who currently dominate the market. Starlink’s new offering provides 50 gigabytes (GB) of monthly data for Ksh1,300 ($10.16), significantly cheaper than Airtel’s Ksh3,000 ($23.44) for a similar amount. Safaricom, the market leader, offers…

Best Data Science Courses and Certifications in the dynamic tech world
1.Data Science Specialization by JHU via Coursera 2. Applied Data Science with Python Specialization by UMich via Coursera 3. Data Science MicroMasters by UC San Diego via edX 4. Dataquest 5. Statistics and Data Science MicroMasters by MIT via edX 6. CS109 Data Science by Harvard 7. Python for Data Science and Machine Learning Bootcamp…



Data science in the world of Technology
What Is Data Science? Data science encompasses the study of extensive data volumes using contemporary tools and methodologies to uncover latent patterns, extract meaningful insights, and inform business decisions. Employing sophisticated machine learning algorithms, data science constructs predictive models derived from diverse data sources presented in various formats. Now, with a grasp of what data…

world’s first rocket pioneer in the…
Elon Musk is in charge of several companies, but SpaceX stands out as particularly exciting due to its ambitious goal of colonizing Mars using reusable rockets. Although Twitter, Tesla, and PayPal were already established before Musk’s involvement, SpaceX was his brainchild. After pocketing $175 million from eBay’s acquisition of PayPal in 2002, Musk invested $100…


How to optimize websites for indexing
1. Create and Submit a Sitemap:Ensure your website has a well-organized sitemap that lists all the important pages and content. Submit this sitemap to major search engines like Google and Bing using their webmaster tools. This helps search engine bots understand the structure of your site. 2. Optimize Robots.txt File:Use the robots.txt file to guide…
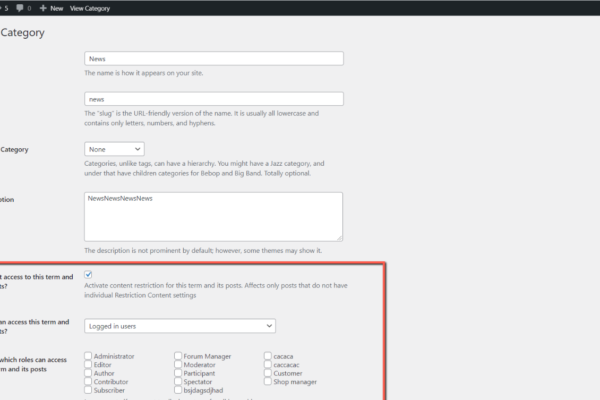
How to activate Ultimate Member plug in
Step 1: Install and Activate Ultimate Member In your WordPress dashboard, navigate to the “Plugins” section. Click on “Add New” and search for “Ultimate Member.” Once you find it, install and activate the plugin. Step 2: Create Memberships Proceed to the “Ultimate Member” section in your dashboard and click on “User Roles.” Here, you can…
Comprehensive Guide to Front-End Development in the year 2023
HTML (HyperText Markup Language) Overview: HTML, the backbone of web development, simplifies the creation of web pages using tags and attributes. It seamlessly integrates multimedia, supports hypertext content, and provides a user-friendly entry point for beginners. Advantages: Disadvantages: CSS (Cascading Style Sheets) Overview: CSS, working in tandem with HTML, defines the style and layout of…

Free website builder in the internet
Note that, these website builders offer free plans, they often come with limited capabilities, such as branded domains, ads, or restricted features. If you’re looking for a more professional and feature-rich website, you might eventually consider upgrading to a paid plan or exploring other options. The best choice depends on your specific needs, so it’s…

The Hidden Wiki verified links in Darknet
Hidden Wiki sites http://s4k4ceiapwwgcm3mkb6e4diqecpo7kvdnfr5gg7sph7jjppqkvwwqtyd.onion/ – OnionLinks v3http://6nhmgdpnyoljh5uzr5kwlatx2u3diou4ldeommfxjz3wkhalzgjqxzqd.onion/ – The Hidden Wikihttp://2jwcnprqbugvyi6ok2h2h7u26qc6j5wxm7feh3znlh2qu3h6hjld4kyd.onion/ – Another Hidden Wikihttp://jgwe5cjqdbyvudjqskaajbfibfewew4pndx52dye7ug3mt3jimmktkid.onion/ – Pug’s Ultimate Dark Web Guidehttp://zqktlwiuavvvqqt4ybvgvi7tyo4hjl5xgfuvpdf6otjiycgwqbym2qad.onion/wiki/index.php/Main_Page – The original hidden wiki Bitcoin anonymity http://y22arit74fqnnc2pbieq3wqqvkfub6gnlegx3cl6thclos4f7ya7rvad.onion/ – Dark Mixer – Anonymous bitcoin mixerhttp://hqfld5smkr4b4xrjcco7zotvoqhuuoehjdvoin755iytmpk4sm7cbwad.onion/ – Mixabit – Bitcoin mixerhttp://mp3fpv6xbrwka4skqliiifoizghfbjy5uyu77wwnfruwub5s4hly2oid.onion/ – EasyCoin – Bitcoin Wallet and Mixerhttp://p2qzxkca42e3wccvqgby7jrcbzlf6g7pnkvybnau4szl5ykdydzmvbid.onion/ – Onionwallet – Anonymous and secure bitcoin wallet and mixerhttp://ovai7wvp4yj6jl3wbzihypbq657vpape7lggrlah4pl34utwjrpetwid.onion/ – VirginBitcoins – Buy freshly mined clean…
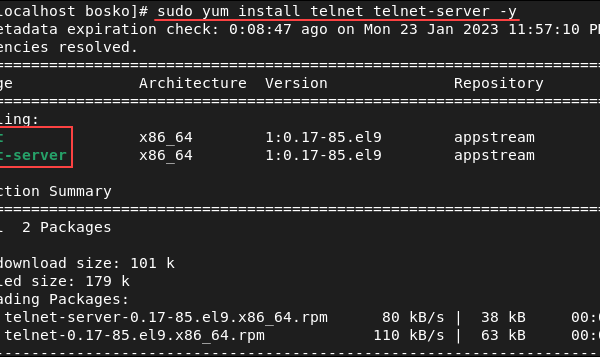
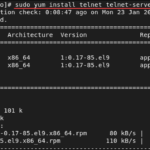
Telnet basics and security in a network
Basics of Telnet: Security Concerns: Recommendations:

China in the lead for orbiting space by 2030
On Thursday, China successfully launched its youngest-ever crew for its orbiting space station, the Shenzhou 17 spacecraft, from the Jiuquan Satellite Launch Center. The three-member crew, with an average age of 38, is part of China’s ambitious plans to put astronauts on the moon before 2030. This initiative reflects the competition for influence between China…

Best bulk messaging companies in the world
1.Twilio: 2.Nexmo (now part of Vonage): 3.Plivo: 4.MessageBird: 5. Clickatell: 6.BulkSMS: 7.Infobip: 8.Sendinblue: 9.Sinch: 10.Twillio SendGrid: 11.Africa’s Talking: provides a variety of communication and payments API products that are everything you need to build high impact mobile engagement solutions. The platform allows on building superior customer engagement experiences without the complexity that comes from working…


Cybersecurity trends in the year 2023
1. Rise of Automotive Hacking As connected vehicles become more ubiquitous, they also become more appealing targets for cybercriminals. Modern automobiles are packed to the brim with automated software that enables connectivity in systems like cruise control, door locks, engine timing, airbags, and driver assistance programs. While convenient for drivers, these interconnected technologies also increase the…

SpaceX launch rises the Space Coast’s total to 60 in a new record for booster flight.
At 8:37 p.m., a Falcon 9 rocket launched from Space Launch Complex 40 at the Cape Canaveral Space Force Station, carrying an additional 23 Starlink satellites from Elon Musk’s company. The booster, with a rich history, had previously flown on several notable missions, including the Crew Demo-2, ANASIS-11, CRS-21, Transporter-1, Transporter-3, and 13 Starlink missions….
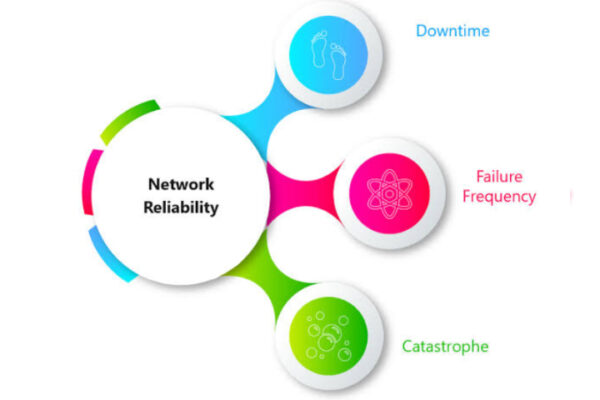
Ways of enhancing network reliability
By implementing these measures, you can significantly improve the reliability and resilience of your network infrastructure.

Important notes on computer network!
A computer network is a collection of two or more interconnected computers, linked either by physical cables (wired) or via wireless connections such as WiFi, facilitating the transmission, exchange, and sharing of data and resources. Creating a computer network involves the utilization of both hardware (such as routers, switches, access points, and cables) and software…

Top Ethical Hacking Tools in the year 2023
Invicti Is a web application security scanner hacking tool to find SQL Injection, XSS, and vulnerabilities in web applications or services automatically. It is usually available on SAAS solution Features:It detects Dead accurate vulnerability with the help of unique Proof-Based Scanning Technology.It requires minimal configuration with a scalable solution. It automatically detects URL rewrite rules…

IPv4 and IPv6 in Networking
IPv4 (Internet Protocol version 4) and IPv6 (Internet Protocol version 6) are two versions of the Internet Protocol that differ in various aspects, including address format, address space, header format, and other features. Here are the key differences between IPv4 and IPv6:

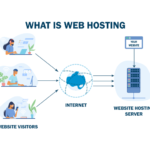
Best types of web hosting in the world
Remember that, When choosing the best type of web hosting, consider factors such as your budget, website traffic, performance requirements, technical expertise, and the level of control you need. It’s very crucial to select a reliable hosting provider with a strong track record of uptime, security, and customer support. https://www.cisco.com/site/us/en/products/security/network-security/index.html#tabs-36b1cf8e54-item-e3508571b8-tab

How to create a website in wordpress
Websites should be regularly updated with fresh content and security patches to keep it running smoothly.
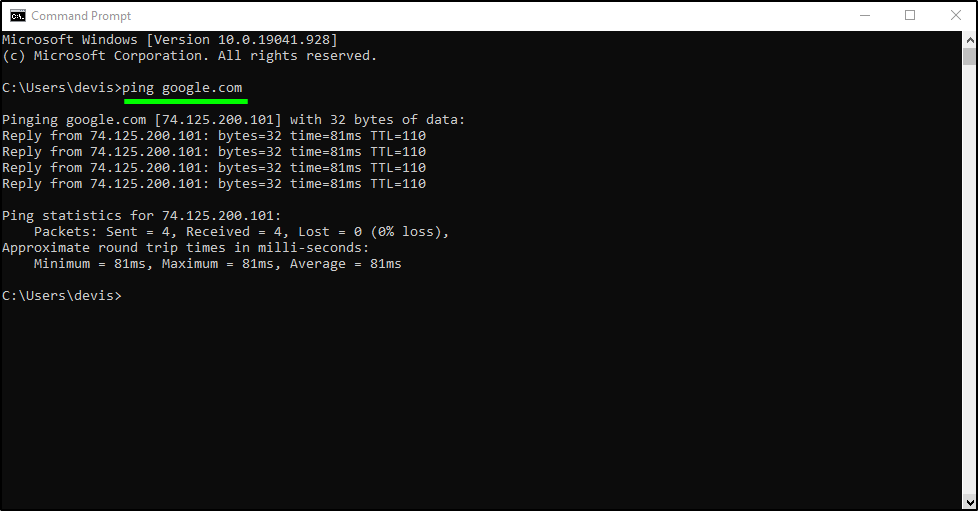
How to ping IP Addresses in cmd
IP Address Definition and Explanation An Internet Protocol (IP) address is the unique identifying number assigned to every device connected to the internet. An IP address definition is a numeric label assigned to devices that use the internet to communicate. Computers that communicate over the internet or via local networks share information to a specific…
How to boost website traffic
Enhance your content using pertinent keywords related to your business, it constitutes the practice of search engine optimization (SEO). Many business connections are established when individuals input specific words or phrases into a search engine to locate a website. Familiarizing yourself with the search terms used by visitors to discover your site facilitates the attraction…

Ethical hacking in the realm of security
The landscape of ethical hacking and penetration testing has transformed significantly due to the emergence of automated tools. Presently, numerous tools are under development that can expedite the testing process. Ethical hacking plays a crucial role in assisting organizations to enhance the protection of their information and systems. Additionally, it serves as one of the…

Risks of digital systems in the world of Tech
Cybersecurity involves safeguarding internet-connected systems, which include hardware, software, and data, from potential cyberthreats. It is a vital practice employed by both individuals and businesses to prevent unauthorized access to data centers and other computerized systems. These threats can take various forms and may target individuals, businesses, or even governments. Some common cybersecurity threats include:…
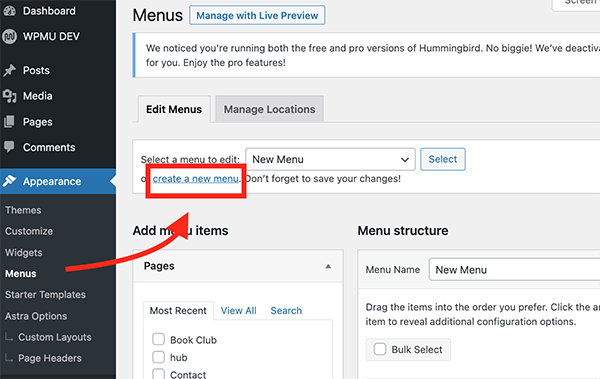
How to create Menus and Submenus in wordpress.
Using the above steps, you can easily create menus and sub-menus in WordPress to organize your site’s navigation and improve user experience.

Best VPNs in the internet
ExpressVPN:ExpressVPN is widely known for its incredibly fast connection speeds, making it an excellent choice for users who prioritize quick and efficient browsing. It boasts a large server network that spans numerous countries, ensuring a stable and reliable connection from various locations worldwide. The service is also highly regarded for its strong security features, including…

Hacking in the context of IT
Hacking refers to the act of gaining unauthorized access to computer systems or networks for various purposes, including testing security, identifying vulnerabilities, or committing cybercrimes. Here are some notes on the advantages and disadvantages of hacking: Advantages of Hacking: Disadvantages of Hacking: It is essential to differentiate between ethical hacking, which aims to improve cybersecurity,…

Best Cybersecurity certifications in the world
Certified Information Systems Security Professional (CISSP) is a globally recognized certification provided by (ISC)². It validates individuals’ expertise in designing, implementing, and managing top-tier cybersecurity programs, making it a prestigious credential in the field. Certified Ethical Hacker (CEH), offered by the EC-Council, is designed for those seeking to understand the mindset of a hacker and…

How to fix double featured image in wordpress.
Some people using WordPress are still having trouble fixing issues they’ve recently come across. Even if they’ve tried everything, they might still see two pictures on one post, or no picture in the post but it shows up in the small picture on the page, or the other way around. If this sounds like your…

Popular website Ad Platforms in the world
Google AdSense is one of the most widely used advertising platforms for website monetization. It enables website owners to display targeted advertisements on their sites and earn revenue based on clicks or impressions. Media.net is a contextual ad network that enables website publishers to display relevant ads to their visitors. It offers contextual ads, display…

Common domains and their purpose
1. .com – Commercial, suitable for most types of businesses and organizations. 2. .org – Typically associated with non-profit organizations and various groups. 3. .net – Originally intended for network-related websites, now used by a variety of businesses and organizations. 4. .gov – Restricted to government agencies and departments. 5. .edu – Reserved for educational…
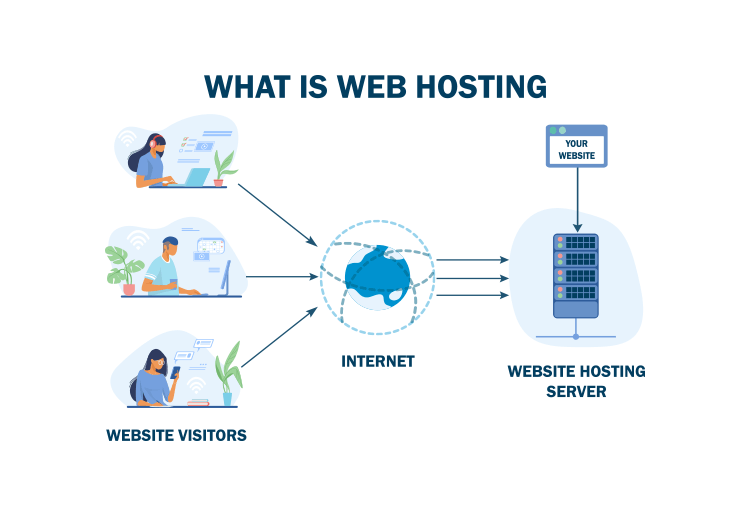
Best Webhosting companies in the world
Each hosting provider has its own unique features and strengths, so it’s essential to consider your specific requirements and preferences when choosing a hosting service.
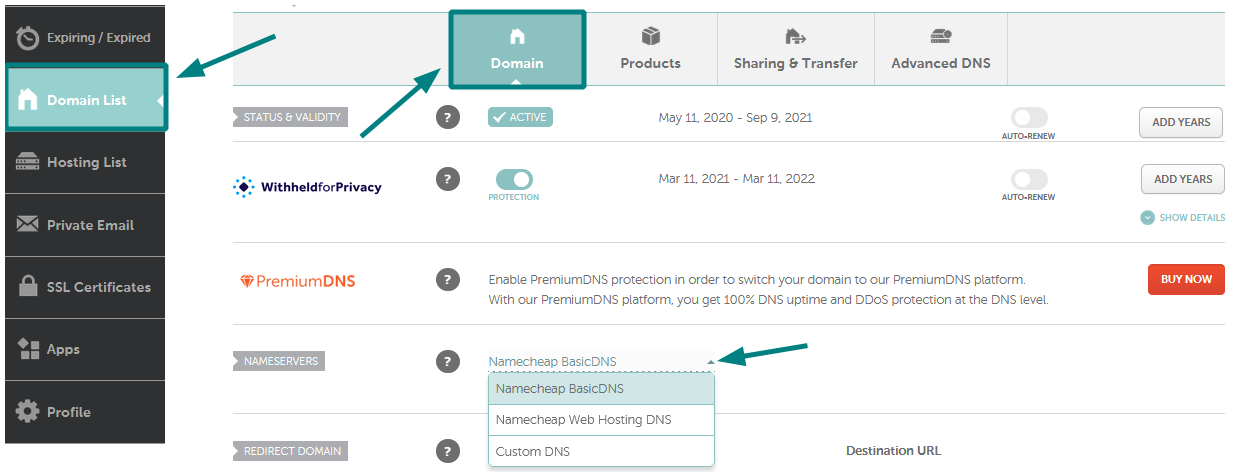
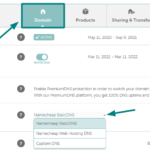
How to change nameservers for a new website
Firstly, go to the website where you bought your domain. After logging in, find the section that manages your domains. Look for the specific domain you want to work on. Inside that section, there should be an option to handle the nameservers. It might be called something like “Nameservers” or “DNS Settings.” When you find…

IBM to build Fault-Tolerant Quantum Computer in the year 2029
IBM Aims to Launch Powerful Quantum Computer by 2029 — Sooner Than Expected IBM has just shared an ambitious plan: it wants to build and launch a large-scale, fault-tolerant quantum computer called IBM Quantum Starling by 2029. This is much sooner than many experts thought possible. If successful, this computer will be incredibly powerful —…