IPv4 (Internet Protocol version 4) and IPv6 (Internet Protocol version 6) are two versions of the Internet...
Year: 2023
Remember that, When choosing the best type of web hosting, consider factors such as your budget, website...
Websites should be regularly updated with fresh content and security patches to keep it running smoothly.
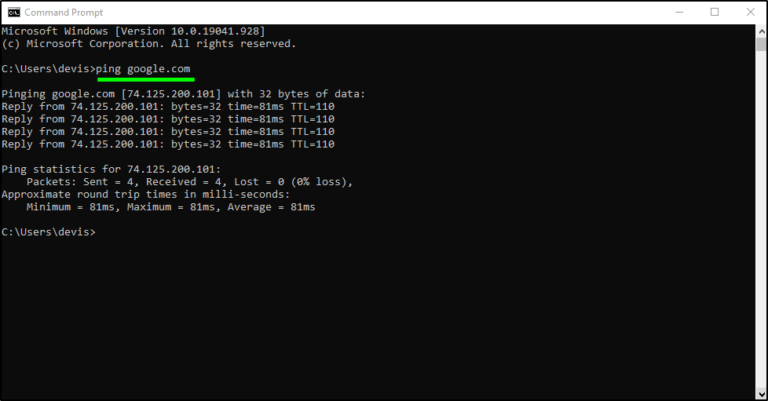
IP Address Definition and Explanation An Internet Protocol (IP) address is the unique identifying number assigned to...
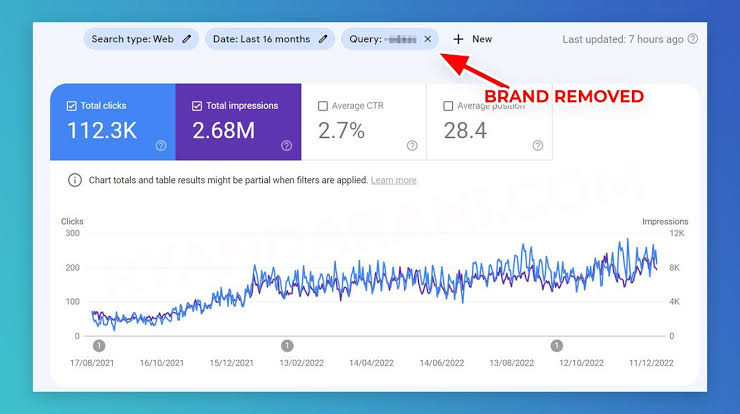
Enhance your content using pertinent keywords related to your business, it constitutes the practice of search engine...
The landscape of ethical hacking and penetration testing has transformed significantly due to the emergence of automated...
Cybersecurity involves safeguarding internet-connected systems, which include hardware, software, and data, from potential cyberthreats. It is a...
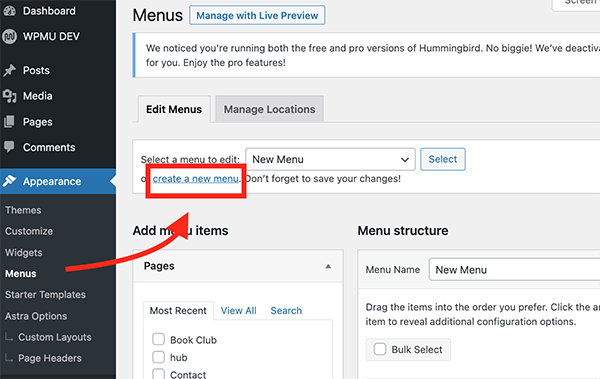
Using the above steps, you can easily create menus and sub-menus in WordPress to organize your site’s...
ExpressVPN:ExpressVPN is widely known for its incredibly fast connection speeds, making it an excellent choice for users...
Hacking refers to the act of gaining unauthorized access to computer systems or networks for various purposes,...