Basics of Telnet:
- Connection Syntax:
- To connect to a remote system using Telnet, you typically use the following syntax in the command line:cssCopy code
telnet [hostname or IP address] [port]
- To connect to a remote system using Telnet, you typically use the following syntax in the command line:cssCopy code
- Default Port:
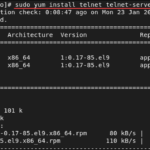
- The default port for Telnet is 23. If you don’t specify a port, Telnet assumes you are connecting to the default port.
- Example:
- For example, to connect to a hypothetical server with IP address 192.168.1.100 on the default Telnet port, you would use:Copy code
telnet 192.168.1.100
- For example, to connect to a hypothetical server with IP address 192.168.1.100 on the default Telnet port, you would use:Copy code
Security Concerns:
- Clear Text Transmission:
- One major security concern with Telnet is that it transmits data, including usernames and passwords, in clear text. This means that if someone intercepts the communication, they can easily read the information being transmitted.
- SSH as a Secure Alternative:
- For secure remote access, it’s recommended to use SSH instead of Telnet. SSH encrypts the communication, providing a much higher level of security.
- Firewall Considerations:
- If you are using Telnet, ensure that your firewall rules are configured to allow traffic on the Telnet port. However, due to security risks, it’s generally better to use more secure protocols.
- Telnet Disablement:
- Many systems and network administrators disable the Telnet service on their servers to enhance security. Instead, they encourage the use of SSH.
Recommendations:
- Use SSH Instead:
- Whenever possible, use SSH for secure remote access. SSH encrypts the data during transmission, providing a higher level of security compared to Telnet.
- Keep Software Updated:
- If Telnet is necessary for a specific reason, ensure that the Telnet server software is kept up to date with the latest security patches.
- Network Segmentation:
- Consider segmenting your network and only allowing Telnet or similar protocols within trusted segments.